API Penetration Testing
Every API endpoint is a potential entry point for your attacker
Protect your API endpoints against cyber threats, protect sensitive data, and ensure a secure communication channel between clients and servers.
Broken Authentication & Session Management (JWT, OAuth vulnerabilities)
API Injections (SQL, XML, JSON injection attacks)
Sensitive Data Exposure (unencrypted data transmission, weak encryption)
Improper Authorisation (access control vulnerabilities, IDOR)
Excessive Data Exposure (overexposing data in API responses)
Lack of Rate Limiting (DoS attacks via brute force)
Security Misconfiguration (default credentials, incorrect permissions)
Insecure Communication (no HTTPS, weak SSL/TLS configurations)
Broken Object Level Authorisation (insecure direct object references)
Insufficient Logging & Monitoring (failure to detect abnormal behaviour)
Every API endpoint is a potential entry point for your attacker
Protect your API endpoints against cyber threats, protect sensitive data, and ensure a secure communication channel between clients and servers.
Broken Authentication & Session Management (JWT, OAuth vulnerabilities)
API Injections (SQL, XML, JSON injection attacks)
Sensitive Data Exposure (unencrypted data transmission, weak encryption)
Improper Authorisation (access control vulnerabilities, IDOR)
Excessive Data Exposure (overexposing data in API responses)
Lack of Rate Limiting (DoS attacks via brute force)
Security Misconfiguration (default credentials, incorrect permissions)
Insecure Communication (no HTTPS, weak SSL/TLS configurations)
Broken Object Level Authorisation (insecure direct object references)
Insufficient Logging & Monitoring (failure to detect abnormal behaviour)
Hardening Your API Endpoints Using Proven Security Frameworks
We identify, analyse, and mitigate security vulnerabilities in both RESTful and SOAP APIs, based on industry-recognised standards such as OWASP API Security Top 10, OWASP API Security Testing, and NIST guidelines.
Our methodology combines manual techniques and automated tools to determine if an attacker can:
Bypass Mechanisms
Bypass authentication and authorisation mechanisms (JWT/OAuth flaws).
Perform Injection Attacks
Perform injection attacks (SQL, XML, command injections).
Expose Sensitive Data
Through weak encryption or misconfigurations.
Access Unauthorised Data
By exploiting broken access control (IDOR, business logic flaws).
Bypassing Rate Limits
Bypass rate-limiting or input validation to flood the API with requests.
Intercept API Traffic
Intercept API traffic through man-in-the-middle (MitM) attacks.
Exploit Insecure API Endpoints
Exploit insecure API endpoints for remote code execution or privilege escalation.
Actionable Recommendations You Can Bring To Stakeholders
We deliver comprehensive, cryptographically signed penetration testing reports that are both verifiable and tamper-proof. Each report includes detailed vulnerability backgrounds, clear impact assessments, and actionable recommendations. And because security is a global concern, our reports are available in 113 languages—ensuring your cross-border teams are always in the know.
Compliance Verification Reporting
The report clearly shows the specific standards the app complies to.
Detailed down to the Test Cases
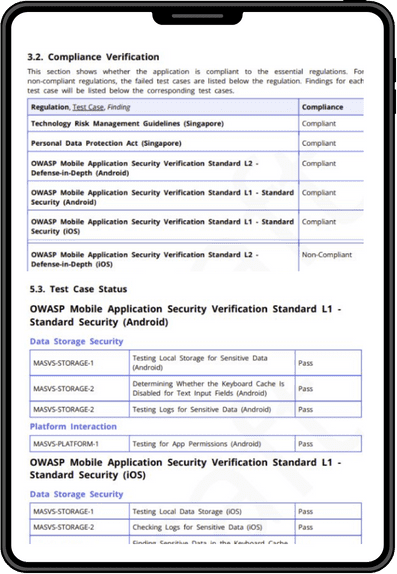

Detailed Background
We explain the vulnerability clear enough for technical and non technical stakeholders to understand.
Impact statements
Explaining the business impact of the vulnerability.
Recommendations
Actionable insights stakeholders can take to remediate gaps.
SPEAK TO AN EXPERT
Know Your Vulnerabilities.
Start Securing your Assets Today.
Experts in Penetration Testing
innovation and IP development
Red Team Providers in Southeast Asia
80,000+ hours of yearly pentesting
Specialists in AppSec
Quality Assurance with Velocity
Other CREST Approved Penetration Testing Services
Web Application
We secure your web applications by identifying injection flaws, authentication bypasses, and business logic vulnerabilities that could expose your systems, ensuring compliance to technical and regulatory standards.
Mobile Application
We secure your iOS and Android applications by identifying code vulnerabilities, insecure data storage, and authentication flaws, ensuring compliance to standards like the OWASP MASVS and more.
Wireless Network
We secure your Wi-Fi and wireless communication systems through targeted testing that identifies encryption flaws, authentication weaknesses, and connection protocol vulnerabilities.
API
We secure your APIs against data breaches and unauthorized access by identifying authentication flaws, injection vulnerabilities, and more in your API endpoints, ensuring compliance to standards like OWASP Top 10 and more.
Thick Client
We secure your desktop applications through thorough testing that identifies local storage vulnerabilities, communication protocol weaknesses, and authentication flaws that could compromise user data.
Active Directory
We secure your Active Directory infrastructure through specialized testing that identifies privilege escalation paths, credential vulnerabilities, and configuration weaknesses that could lead to domain compromise.
Other CREST Approved Penetration Testing Services
Mobile Application
We secure your iOS and Android applications by identifying code vulnerabilities, insecure data storage, and authentication flaws, ensuring compliance to standards like the OWASP MASVS and more.
Web Application
We secure your web applications by identifying injection flaws, authentication bypasses, and business logic vulnerabilities that could expose your systems, ensuring compliance to technical and regulatory standards.
Network
We secure your network infrastructure by identifying misconfigurations, weak protocols, and access control flaws across routers, switches, servers, and endpoints. We ensure compliance to many industry standards.
Wireless Network
We secure your Wi-Fi and wireless communication systems through targeted testing that identifies encryption flaws, authentication weaknesses, and connection protocol vulnerabilities.
Thick Client
We secure your desktop applications through thorough testing that identifies local storage vulnerabilities, communication protocol weaknesses, and authentication flaws that could compromise user data.
Active Directory
We secure your Active Directory infrastructure through specialized testing that identifies privilege escalation paths, credential vulnerabilities, and configuration weaknesses that could lead to domain compromise.

